The ____ Commercial Site Focuses on Current Security Tool Resources
Net accounts sets password and logon requirements for users. Shibboleth is an identity federation method providing single sign-on capabilities and enabling websites to make informed authorization decisions for access.

Malicious Threat An Overview Sciencedirect Topics
Configuration An __________ item is a hardware or software item that is to.
. Start studying Chapter 12. Encourage security-conscious employee behavior. For security professionals threat assessment is also used to describe a process through which your operational personnel observe and identify potential immediate or imminent threats eg active shooters terrorists criminals.
True Rehearsal adds value by exercising the procedures identifying shortcomings and providing security personnel the opportunity to improve the security plan before it is needed. Poor password security is one of the biggest threats to modern enterprise security. Both tools are web-based applications that support all steps in the risk management process.
It also focuses on preventing application security defects and vulnerabilities. The PRIMARY objective of security awareness is to. Which of the following should be implemented to provide the MOST secure environment.
While investigating a virus infection a security analyst discovered the following on an employee laptop. Multiple folders containing a large number of newly released movies and music files. The government most commonly uses these risk management tools.
The _____ commercial site focuses on current security tool resources. The _____ commercial site focuses on current security tool resources. The _____ commercial site focuses on current security tool resources.
Which of the following security standards is internationally recognized as the standards for sound security practices and is focused on the standardization and certification of an organizations Information Security Management System ISMS. Read more about it here. Enterprise risk management ERM 1 is a fundamental approach for the management of an organization.
Focus Area 6. But because personal computers are just that personal staff behavior cant always be dictated without. Analysis of the file system misses the systems volatile memory ie RAM.
Net share creates removes or manages shared resources. COVID-19 is stressing many pieces of the economy from hospitals and healthcare to delivery services and logistics. Some forensics tools focus on capturing the information stored here.
Net session lists or disconnects sessions between a computer and other computers on the network. Ensure that security policies are read and understood. Volatility is the memory forensics framework.
During a monthly vulnerability scan a server was flagged for being vulnerable to an Apache Struts exploit. Risk Radar and Risk Radar Enterprise. Security Assertion Markup Language SAML is an identity federation format used to exchange authentication information between the principle the service provider and the identity provider.
Introduction to Security Management. The Forum of Incident Response and Security Teams FIRST is an international consortium of computer incident response and security teams who work together to handle computer security incidents and to promote preventive activities. Question 590 Topic 1.
The mission of FIRST is to provide its members with technical information and tools methods assistance and. The _____ commercial site focuses on current security tool resources. Learn vocabulary terms and more with flashcards games and other study tools.
An air gapped computer network. A company is developing a new secure technology and requires computers being used for development to be isolated. Because system security is the aggregate of individual component security system boundaries must encompass individual users and their workstations.
There are many commercial based systems that can provide Intrusion Prevention Intrusion Detection and analyses. The net command is a very important commandSome common net commands include these. You should have a good ticketing system documentation system and inventory system.
Net start starts a network. This extends cybersecurity concerns to cyberphysical challenges especially given the increase in automated services and systems. A security audit performed on the internal network of an organization by the network administration is also known as ___________.
You should also stay on top of all the security trends as well by connecting to websites and security feeds that will update you on current events. A white-hat hacker is a good guy who uses his skills for defensive purposes. Meet legal and regulatory requirements.
A large amount of PHI data. Provides either direct support or indirect tools that. It can rebuild registries from both current and previous Windows installations.
Passwords are the most common and easiest-to-use authentication system in existence. Packet Storm An __________ item is a hardware or software item that is to. Question 62 Topic 1.
A perimeter firewall and IDS. The _____ mailing list includes announcements and discussion of a. A Nmap-hackers B Packet Storm C Security Focus.
A procedure that compares the current state of a network segment the systems and services it offers against a known previous state of that same network segment the baseline of systems and services. Carrying out a risk assessment allows an organization to view the application portfolio holisticallyfrom an attackers perspective. A security risk assessment identifies assesses and implements key security controls in applications.
Upon further investigation the developer responsible for the server informs the security team that Apache Struts is not installed on the server. Question 123 Topic 1. Budget estimates to acquire specific security tools 14.
The _____ commercial site focuses on current security tool resources. Most employees have dozens of online accounts that are accessed by providing a username often their email address and a password. Based on the landmark work of the Committee of Sponsoring Organizations of the Treadway Commission COSO 2 in the 1990s its seminal Enterprise Risk Management Integrated Framework 3 has become a primary tool.
Commercial site focuses on current security tool resources. Mailing list includes announcements and discussion of a leading open-source IDPS. Account for cyberphysical systems security challenges.
Effective security strikes a balance between protection and convenience. Put employees on notice in case follow-up action for noncompliance is necessary. Many commercial tools are available to support program risk management efforts.
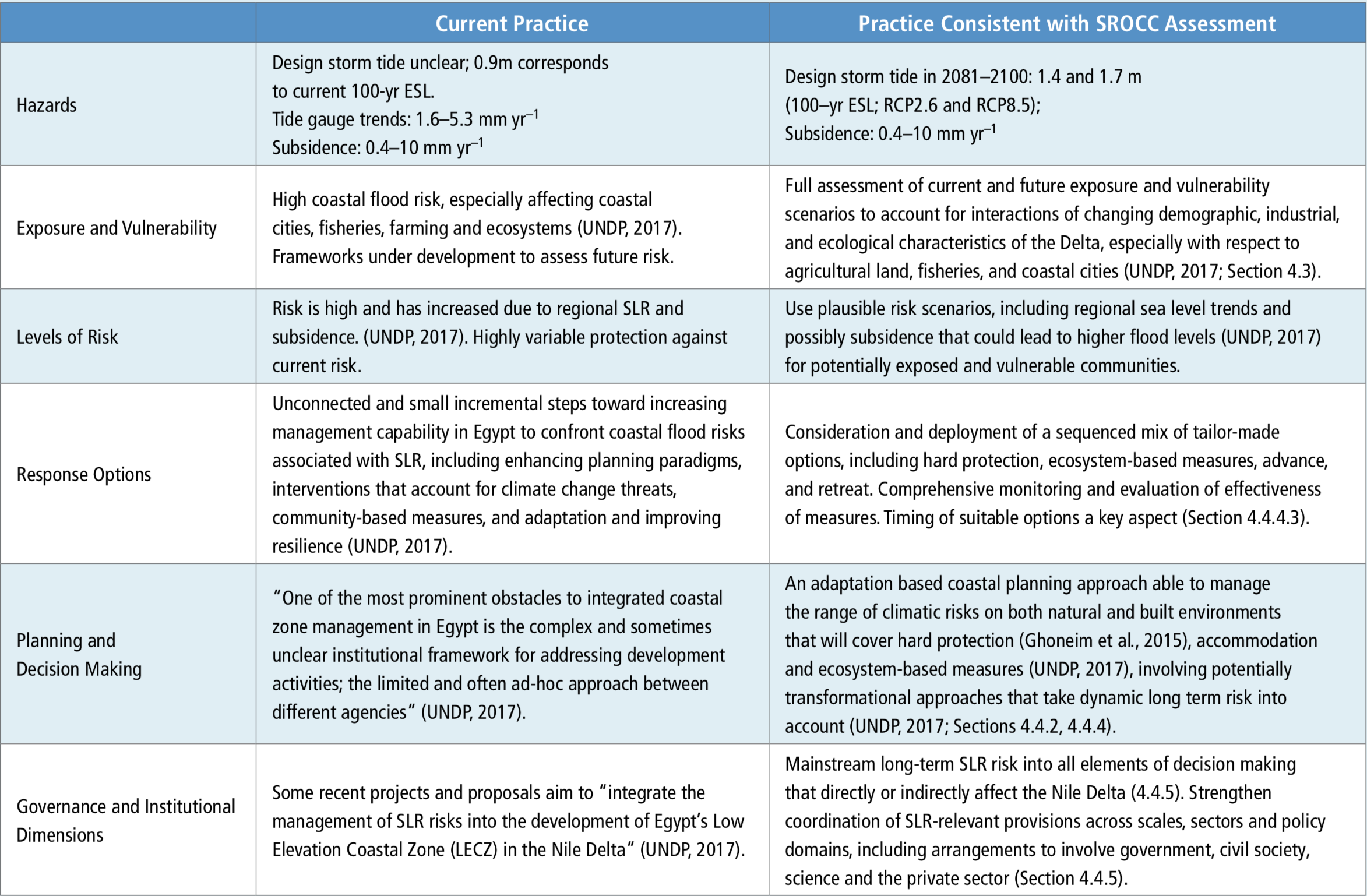
Chapter 4 Sea Level Rise And Implications For Low Lying Islands Coasts And Communities Special Report On The Ocean And Cryosphere In A Changing Climate

The Seven Itil 4 Guiding Principles Bmc Software Blogs
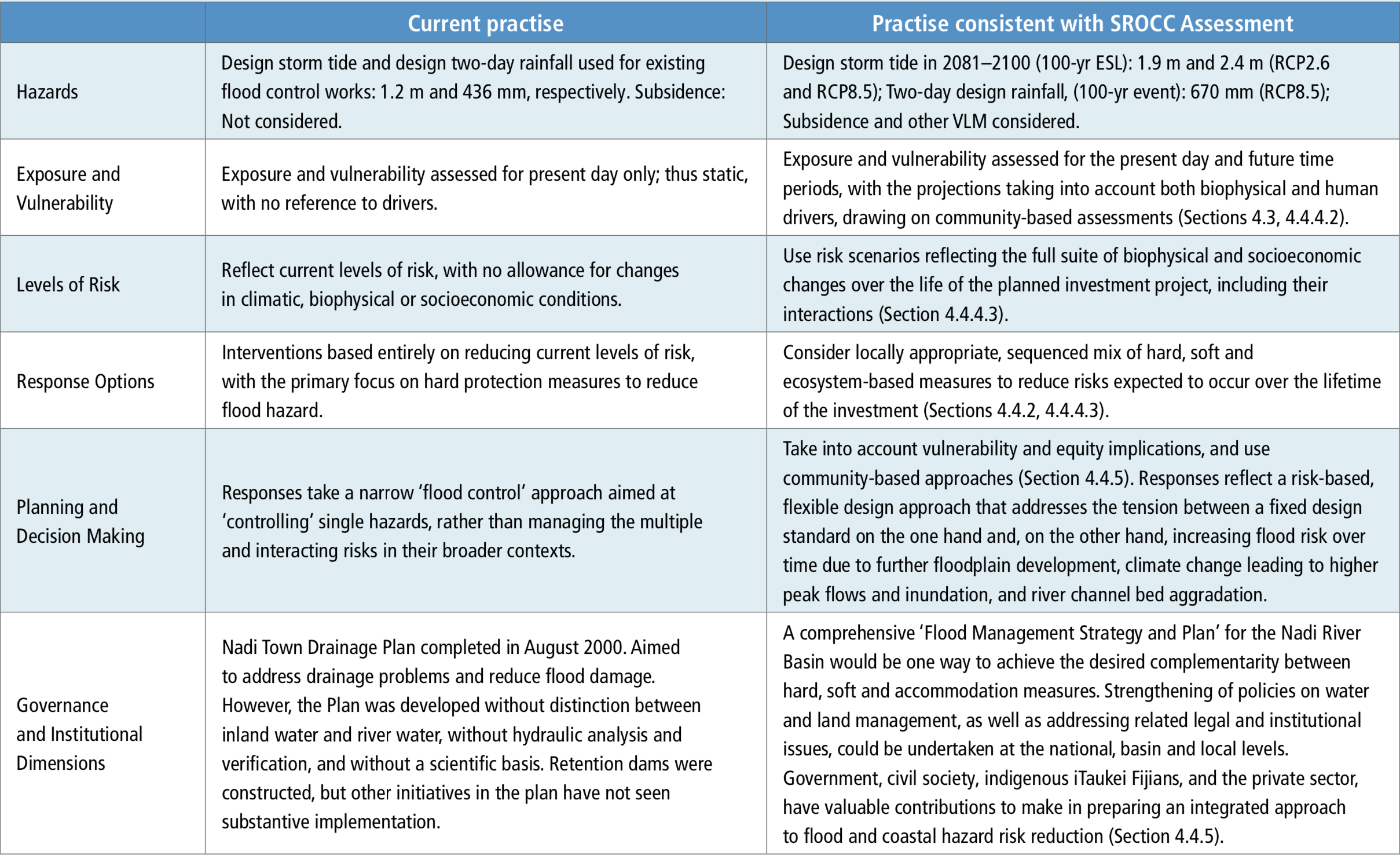
Chapter 4 Sea Level Rise And Implications For Low Lying Islands Coasts And Communities Special Report On The Ocean And Cryosphere In A Changing Climate

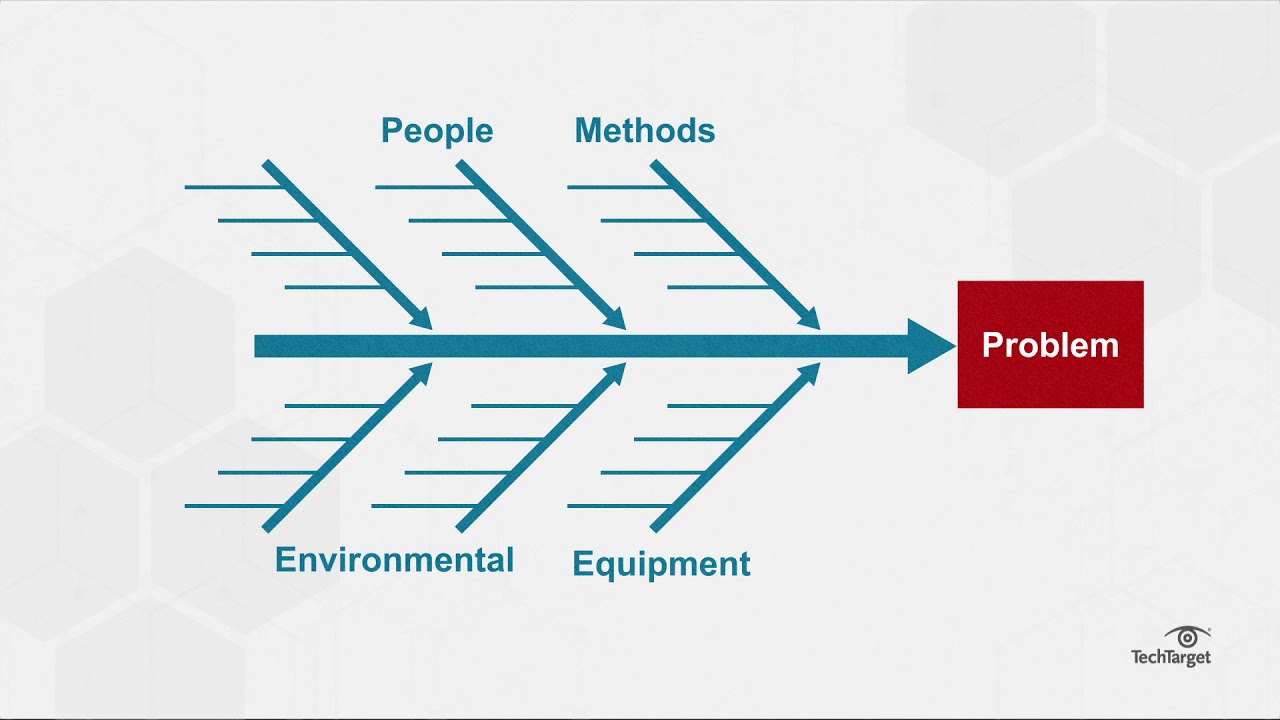
What Is A Fishbone Diagram Ishikawa Cause And Effect Diagram
Comments
Post a Comment